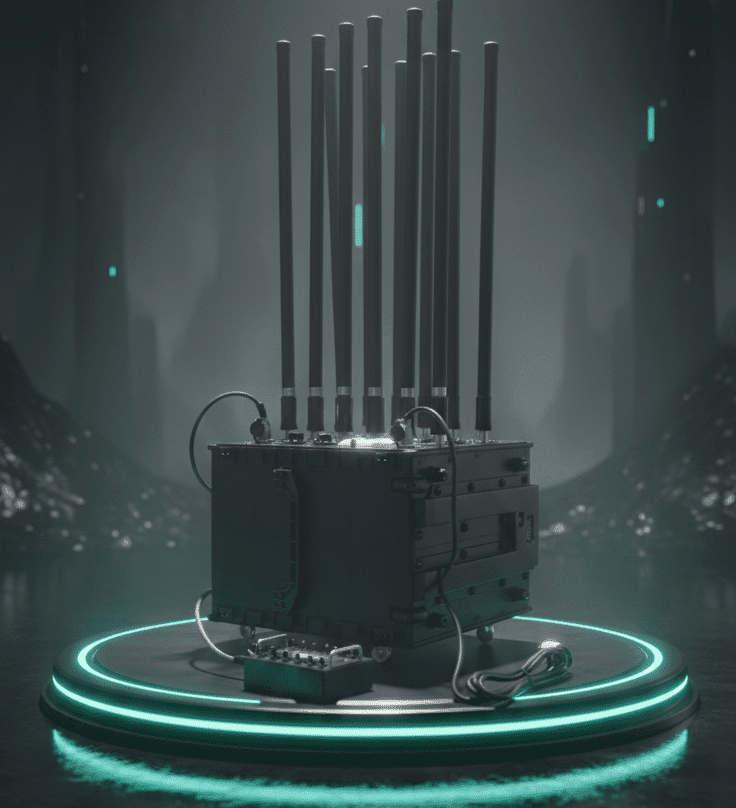
DJY 700 Overview
Engineered for Modern Aerial Threats
JDY-700 is a high-power, long-range counter-drone defense system designed for wide-area airspace protection. It integrates advanced detection, multi-sensor tracking, and robust electronic countermeasures to secure critical infrastructure, military installations, and strategic high-value zones against evolving UAV threats.
System Capabilities
Core Performance
Advanced technological capabilities defining the JDY-700 dominance in wide-area operational environments.
Drone Detection
Advanced sensors detect unauthorized aerial threats
Signal Disruption
Precision interference disrupts hostile control signals
Remote Monitoring
Real-time command hub integration alerts
Airspace Protection
Comprehensive perimeter security and defense
Defining Capabilities
Key Features
Engineered for mission-critical performance in the most demanding environments
Multi-Band Interference
Disrupts drones across multiple frequency bands.
Our system employs advanced multi-band interference technology to effectively neutralize a wide spectrum of drone communication and navigation signals, ensuring comprehensive airspace denial.
Long-Range Coverage
Extensive detection and mitigation range. Achieve superior situational awareness with our long-range detection capabilities, extending your protective perimeter far beyond immediate threats and providing ample reaction time.
Rugged Industrial Design
Built for extreme environments and durability. Engineered to withstand the harshest operational conditions, our system features a rugged, industrial-grade design ensuring reliability and performance in any climate or terrain.
Rapid Deployment
Quick and efficient setup for immediate protection. Designed for operational agility, our counter-drone system can be rapidly deployed and activated, providing immediate protective measures against evolving aerial threats with minimal setup time.
Continuous Operation
Uninterrupted protection, 24/7 monitoring. Ensure constant vigilance with a system built for continuous, 24/7 operation. Our robust architecture guarantees uninterrupted performance and persistent airspace security.
Secure & Controlled Usage
Authorized operation with robust security protocols. Operate with confidence. Our system incorporates advanced security protocols and controlled access mechanisms, ensuring usage is strictly authorized and compliant with regulatory standards.
System Workflow
How It Works
A streamlined defense protocol designed for rapid response and maximum effectiveness
Detect Unauthorized Drones
Our advanced sensor array continuously scans the designated airspace, utilizing multi-spectral detection to identify and classify all aerial objects, distinguishing between authorized and unauthorized drones with high precision.
Locate the Drone and Operator
Leveraging advanced signal direction-finding and tracking algorithms, JDY-700 identifies drone flight trajectories and estimates operator locations in real time, providing enhanced situational awareness and accurate threat assessment across wide operational areas.
Neutralize the Threat Safely
Once a threat is confirmed, JDY-700 initiates high-power, targeted electronic countermeasures, including signal disruption and navigation interference, forcing hostile drones to hover, retreat, or land safely while minimizing collateral impact.
Monitor, Log, and Respond
All detection and mitigation activities are displayed on a secure monitoring interface. Operators receive real-time alerts, event logs, and threat status updates for coordinated response and post-incident analysis.
Deployment Scenarios
Mission Applications
Proven protection across critical sectors and high-security environments
Airports & Aviation
Protecting airport perimeters and flight paths from unauthorized drone incursions to ensure passenger safety and operational continuity.
- Key Benefits: Enhanced air traffic safety, prevention of flight disruptions, compliance with aviation regulations, rapid threat neutralization.
- Challenges Addressed: Drone-related flight delays/cancellations, potential for collisions with aircraft, security breaches, unauthorized surveillance.
Critical Infrastructure Protection
Safeguarding vital national assets such as power plants, water treatment facilities, and communication hubs from aerial threats and espionage.
- Key Benefits: Uninterrupted operation of essential services, protection against sabotage, prevention of data exfiltration, enhanced physical security.
- Challenges Addressed: Industrial espionage, physical attacks via drones, unauthorized data collection, disruption of critical services.
Border & Coastal Security
Monitoring and securing national borders and coastal regions against illegal crossings, smuggling, and reconnaissance by hostile entities using drones.
- Key Benefits: Improved border surveillance, interdiction of illicit activities, enhanced national security, rapid response to aerial threats.
- Challenges Addressed: Cross-border smuggling, illegal immigration, reconnaissance by adversarial forces, difficulty in monitoring vast areas.
Public Event Security
Ensuring the safety and security of large public gatherings, concerts, and sporting events by neutralizing unauthorized drones that pose risks to attendees.
- Key Benefits: Enhanced public safety, prevention of security incidents, protection of VIPs, compliance with event security protocols.
- Challenges Addressed: Terrorist threats, unauthorized filming/surveillance, disruption of events, potential for dropping dangerous payloads.
Military & Defense Sites
Providing robust counter-drone capabilities for military bases, training grounds, and forward operating positions to protect personnel and sensitive assets.
- Key Benefits: Protection of classified information, prevention of reconnaissance, enhanced force protection, operational readiness.
- Challenges Addressed: Adversarial intelligence gathering, direct attacks, unauthorized surveillance of sensitive operations, maintaining air superiority.
Authorized Use Only
Designed for professional defense, government, and authorized security personnel.
Global Deployment
Suitable for fixed, mobile, and temporary deployments worldwide.
Enterprise Integration
Seamlessly integrates with existing C2 systems and security infrastructure.
Important Notice
This counter-drone defense system is a controlled technology designed for authorized security and defense applications only. Deployment requires proper licensing, regulatory approval, and trained personnel. Unauthorized use, sale, or export is strictly prohibited and may result in severe legal consequences. All operators must comply with local, national, and international laws governing radio frequency interference and airspace security.
Reviews
There are no reviews yet.